Wireless Attacks
The WIPS Wireless Attacks Screen displays information about wireless attacks on the network including AP attacks and Client attacks. To access the WIPS Wireless Attacks screen, click on Wireless > WIPS > Wireless Attacks under the “Configure” section of the OmniVista Cirrus Menu.
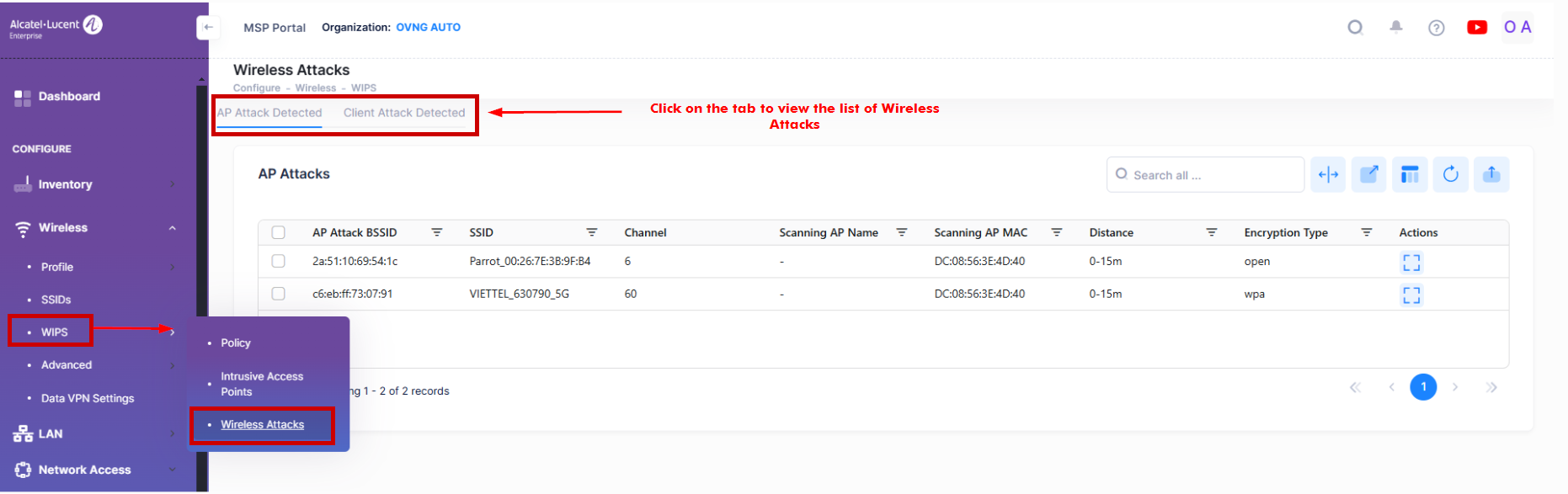
By default, the “AP Attack Detected” list is displayed. Click on Client Attack Detected to display that list.
Devices in the “AP Attack Detected” list can be added to the “Friendly AP” list by selecting the device(s) in the list, then selecting Add to Friendly from the “Actions” drop-down menu.
Devices in the “Client Attack Detected” list can be added to the Client Blocklist by selecting the device(s) in the list, then selecting Add to Client Blocklist from the “Actions” drop-down menu.
The devices are not moved from one list to the other, but added to the other list, so that the WIPS application can maintain a history of device states.
AP Attack Detected
Channel - Working channel of the radio frequency of the attack AP.
Distance - Estimated distance between the attack AP and the valid detecting AP.
Encryption Type - Encryption method of the ESSID broadcast by the attack AP.
Signal Strength - RSSI of the attack AP.
Last Detected Time - The latest time that the attack AP was seen by the detecting AP.
Attack AP BSSID - BSSID of the attack AP.
SSID - ESSID broadcast by the attack AP.
Scanning AP Name - Name of the valid AP that detected the attack AP.
Scanning AP MAC - MAC address of valid AP that detected the attack AP.
Attached Clients - Clients associated to the attack AP.
Attack Detection - The Attack Detection Policy used (e.g., Detect Valid Station Misassociation).
Client Attack Detected
Channel - Working channel of the attack client.
Distance - Distance between the attack client and the detecting AP.
Encryption Type - Encryption method of the SSID to which the attack client is associated.
Signal Strength - RSSI of the attack client.
Last Detected Time - The latest time that the attack client was seen by the detecting AP.
Attack Client MAC - MAC address of the attack client.
In Blocklist - Whether or not the client is in the Blocklist.
SSID - ESSID to which the attack client is associated.
Attack AP MAC - MAC address of the attack AP to which the client is associated.
Attack Detection - The Attack Detection Policy used (e.g., Detect Valid Station Misassociation).
See WIPS Top N Attacks Online help for more information.