WIPS Top N Attacks
The WIPS Top N Attacks Screen displays information about wireless attacks on the network including AP attacks and Client attacks. To access the WIPS Top N Attacks screen, click on Network > Analytics > WIPS Analytics and select Top N Attacks tab under the “Monitor” section of the OmniVista Cirrus Menu.
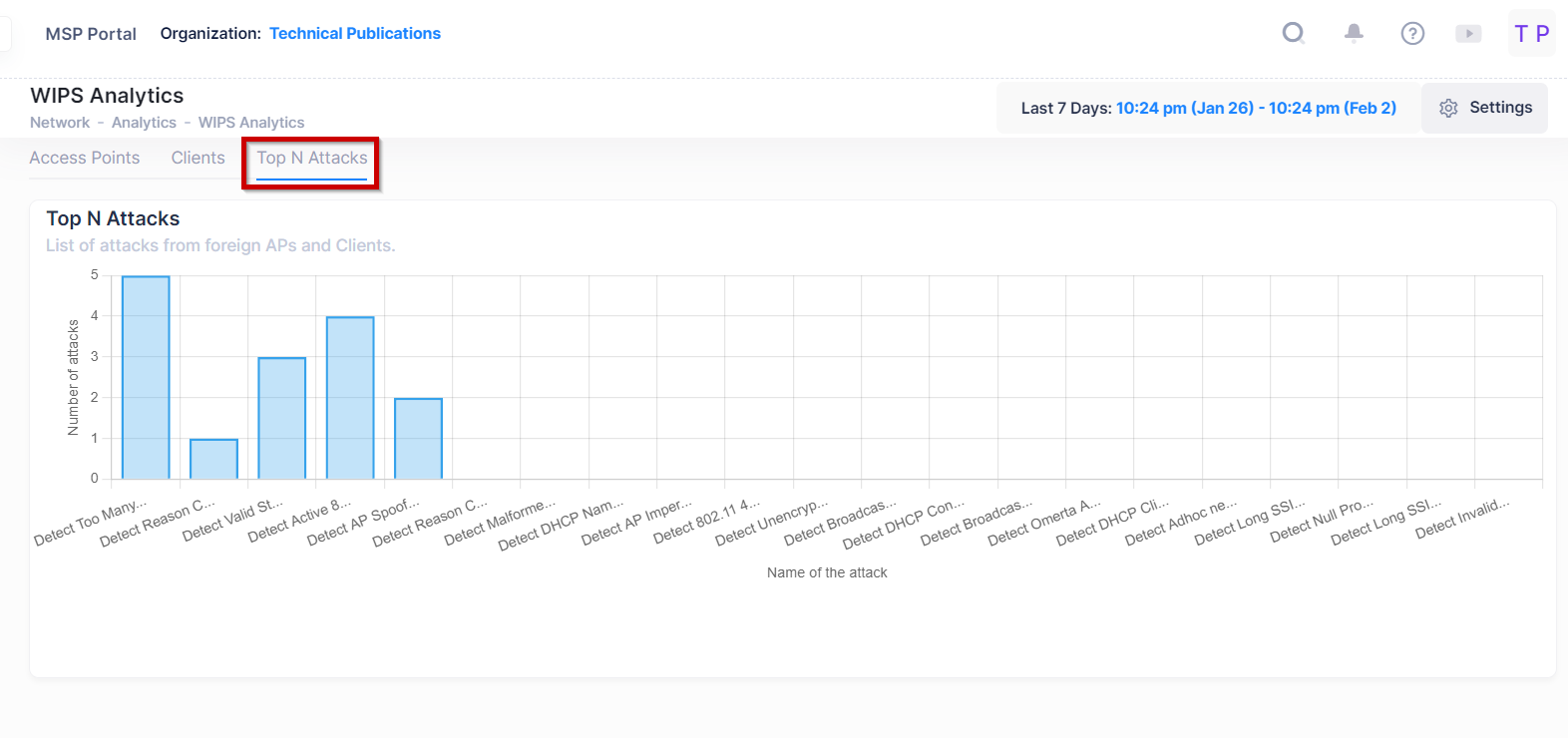
The Top N Attacks screen provides a chart of Wireless attacks observed in the network from foreign Access points and Clients based on the type of attack detected during the specified time window range. The graph displays the top 5 attacks (by default) observed in the network.
Below is the list of multiple attacks originating from foreign APs and the attacks originating from wireless clients.
Detect AP Spoofing - An AP Spoofing attack involves an intruder sending forged frames that are made to look like they are from a valid AP.
Detect Broadcast De-authentication - A de-authentication broadcast attempts to disconnect all clients in range. Rather than sending a spoofed de-authentication frame to a specific MAC address, this attack sends the frame to a broadcast address.
Detect Broadcast Disassociation - By sending disassociation frames to the broadcast address (FF:FF:FF:FF:FF:FF), an intruder can disconnect all stations on a network for a widespread DoS.
Detect Adhoc Networks using VALID SSID - If an unauthorized ad hoc network is using the same SSID as an authorized network, a valid client may be tricked into connecting to the wrong network. If a client connects to a malicious ad hoc network, security breaches or attacks can occur.
Detect Long SSID - Detects long SSIDs with more than 32 characters in the name.
Detect AP Impersonation - In AP impersonation attacks, an AP assumes the BSSID and ESSID of a valid AP. AP impersonation attacks can be done for person-in-the-middle attacks, a rogue AP attempting to bypass detection, or a Honeypot attack.
Detect Adhoc Networks - An ad hoc network is a collection of wireless clients that form a network among themselves without the use of an AP. If the ad hoc network does not use encryption, it may expose sensitive data to outside eavesdroppers. If a device is connected to a wired network and has bridging enabled, an ad-hoc network may also function like a rogue AP. Additionally, ad-hoc networks can expose client devices to viruses and other security vulnerabilities.
Detect Wireless Bridge - Wireless bridges are normally used to connect multiple buildings together. However, an intruder could place (or have an authorized person place) a wireless bridge inside the network that would extend the corporate network somewhere outside the building. Wireless bridges are somewhat different from rogue APs in that they do not use beacons and have no concept of association. Most networks do not use bridges. In these networks, the presence of a bridge is a signal that a security problem exists.
Detect Null Probe Response - A null probe response attack has the potential to crash or lock up the firmware of many 802.11 NICs. In this attack, a client probe-request frame will be answered by a probe response containing a null SSID. Many popular NIC cards will lock up upon receiving such a probe response.
Detect Invalid Address Combination - In this attack, an intruder can cause an AP to transmit de-authentication and disassociation frames to its clients. Triggers that can cause this condition include the use of broadcast or multicast MAC address in the source address field.
Detect Reason Code Invalid of De-authentication - De-authentication packets with invalid reason code will be classified as an attack.
Detect Reason Code Invalid of Disassociation - Disassociation packets with invalid reason code will be classified as an attack.
Detect Valid Station Mis-association - This feature does not detect attacks, but rather monitors valid wireless clients and their association within the network. Valid client mis-association is potentially dangerous to network security. The four types of mis-association monitored are:
Valid Client Associated to a Rogue - A valid client that is associated to a rogue AP
Valid Client Associated to an Interfering AP - A valid client that is associated to an interfering AP
Valid Client Associated to a Honeypot AP - A honeypot is an AP that is not valid but is using an SSID that has been designated as valid
Valid Client in Ad Hoc Connection Mode - A valid client that has joined an ad hoc network
Detect Omerta Attack - Omerta is an 802.11 DoS tool that sends disassociation frames to all clients on a channel in response to data frames. The Omerta attack is characterized by disassociation frames with a reason code of 0x01. This reason code is “unspecified” and is not be used under normal circumstances.
Detect Unencrypted Valid Client - A valid client that is passing traffic in unencrypted mode is a security risk. An intruder can sniff unencrypted traffic (also known as packet capture) with software tools known as sniffers. These packets are then reassembled to produce the original message.
Detect 802.11 40MHZ Intolerance Setting - When a client sets the HT capability “intolerant bit” to indicate that it is unable to participate in a 40MHz BSS, the AP must use lower data rates with all of its clients. Network administrators often want to know if there are devices that are advertising 40MHz intolerance, as this can impact the performance of the network.
Detect Active 802.11n Greenfield Mode - When 802.11 devices use the HT operating mode, they can’t share the same channel as 802.11a/b/g clients. Not only can they not communicate with legacy devices, the way they use the transmission medium is different, which would cause collisions, errors and retransmissions.
Detect DHCP Client ID - A client which sends a DHCP DISCOVER packet containing a Client-ID tag (Tag 61) which doesn't match the source MAC of the packet may be doing a DHCP denial-of-service to exhaust the DHCP pool.
Detect DHCP Conflict - Clients which receive a DHCP address and continue to use a different IP address may indicate a mis-configured or spoofed client.
Detect DHCP Name Change - The DHCP configuration protocol allows clients to optionally put the hostname in the DHCP Discover packet. This value should only change if the client has changed drastically (such as a dual-boot system). Changing values can often indicate a client spoofing/MAC cloning attack.
Detect Too Many Auth Failure Client - Client which attempts to connect to Stellar AP but fails to pass the authentication for too many times, indicating an attack client.
Detect Malformed Frame-Assoc Request - Some wireless drivers used in access points do not correctly parse the SSID information element tag contained in association request frames. A malicious association request with a null SSID can trigger a DoS or potential code execution condition on the targeted device.
Detect Long SSID At Client - Detect long SSID in the wireless environment based on packets sent by clients.
Detect Reason Code Invalid of De-authentication - Detect invalid De-authentication Reason Code.
Detect Reason Code Invalid of Disassociation - Detect invalid Disassociation Reason Code.
WIPS Summary Settings
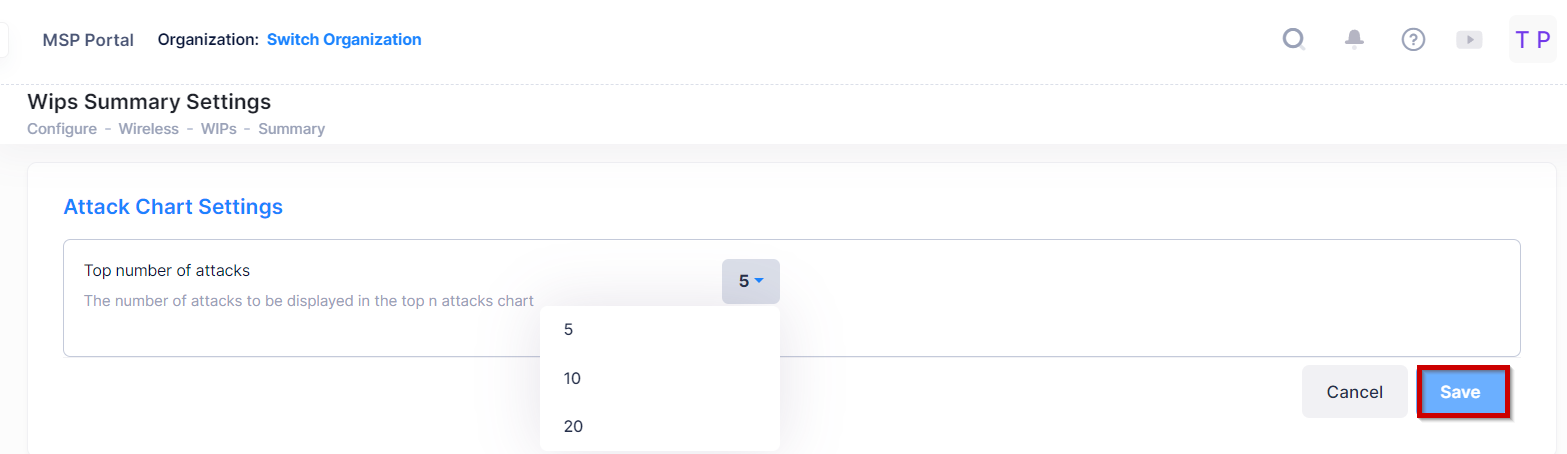
You can set the number of attacks to be displayed in the Top N Attacks by clicking on the settings tab at the top of the screen, it redirects you to the WIPS Summary Settings screen.
You can change the Attack Chart settings from here by selecting the top number of attacks from the drop-down list. (By default = 5, or 10 or 20). Click on the Save button to apply the changes.
See the Wireless Attacks Online help for more information.