Authentication Records
The Authentication Records screen displays a list of all devices authenticated through UPAM. There is an option to view authentication records for clients currently online and an option to review historical client records. You can also display additional information about a specific Authentication Record. Use this information to troubleshoot authentication failures.
To access the Authentication Records screen, click on Network > Access Records > Authentication Records under the “Monitor” section of the OmniVista Cirrus Menu.
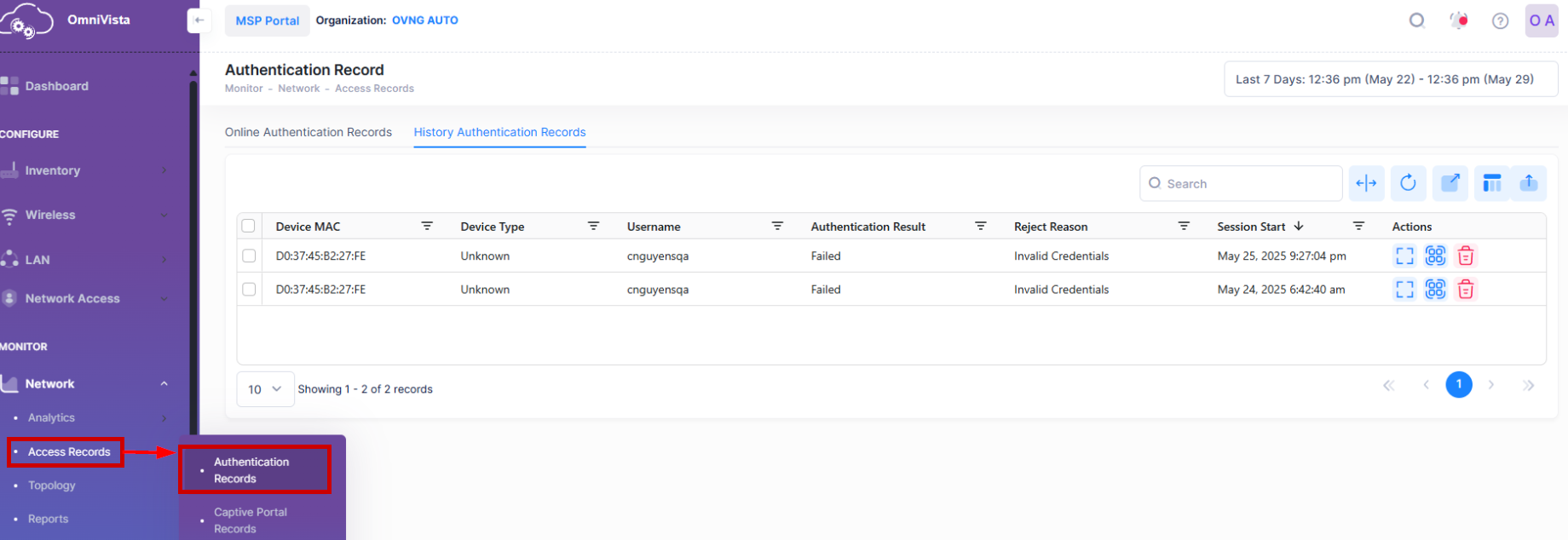
By default, the Online Authentication Records List is displayed on the Authentication Records screen. This is a list of clients currently online. Click on the History Authentication Records tab to see a history of client authentication records. You can also select a specific time window range from the date range to filter the history of Authentication Records by starting time. For example:
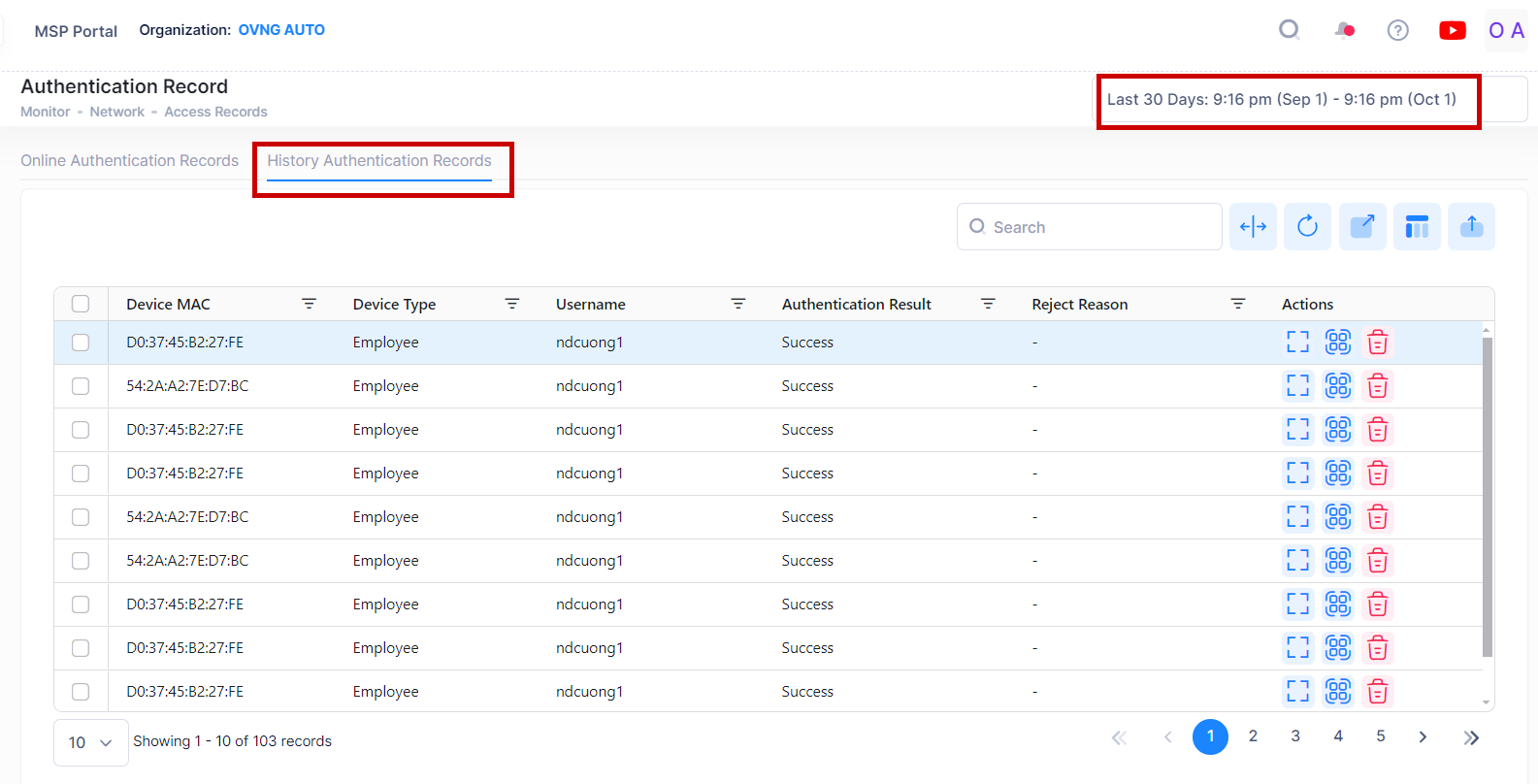
On the History Authentication Records screen, you have the following additional options:
Immediately log a user out of the network. The user will have to log in again to connect to the network.
Generate a PSK
To generate a PSK for one or more devices, select the records in the History Authentication Records List and click on Actions, then select Generate PSK from the drop-down menu. You can also click on the Generate PSK icon under the “Actions” column next to an individual record.
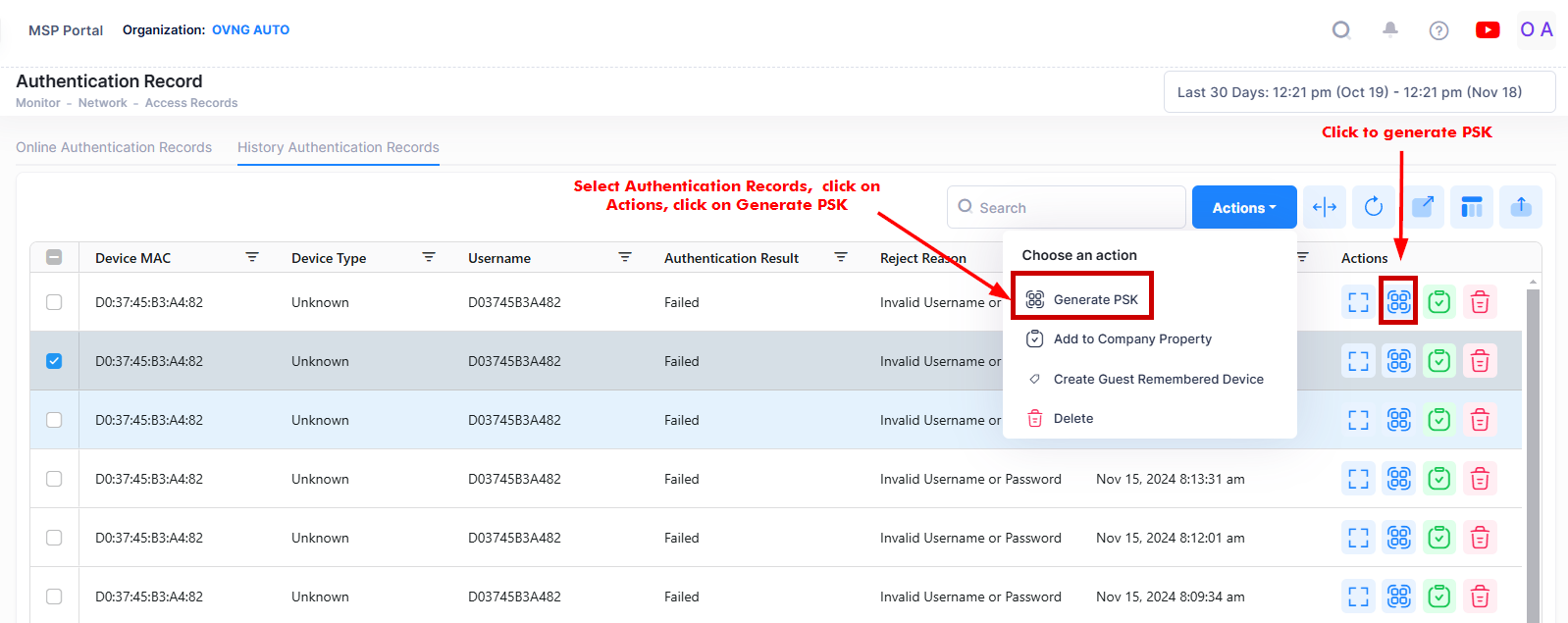
The Generate DSPSK for Authentication Record modal opens.
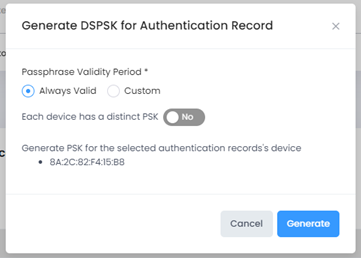
Select the Passphrase Validity Period (Always Valid or Custom) and whether each device will have a distinct PSK, then click on Generate. The device(s) associated with the record(s) will be added to the Company Property List as Device Specific PSK Devices. The PSK Passphrase for the device(s) is automatically generated by OmniVista Cirrus based on the device MAC Address and Session Time. The PSK Passphrase can be obtained and printed from the Company Property Screen. You can generate a PSK for any Authentication Record. See the Company Property online help for more information.
Generate an Employee Account
To generate the Employee Accounts for the Authentication Records, select the records in the History Authentication Records list and click on Actions, then select Add to Employee Account from the drop-down menu. You can also click on the Add to Employee Account icon under the “Actions” column next to an individual record.
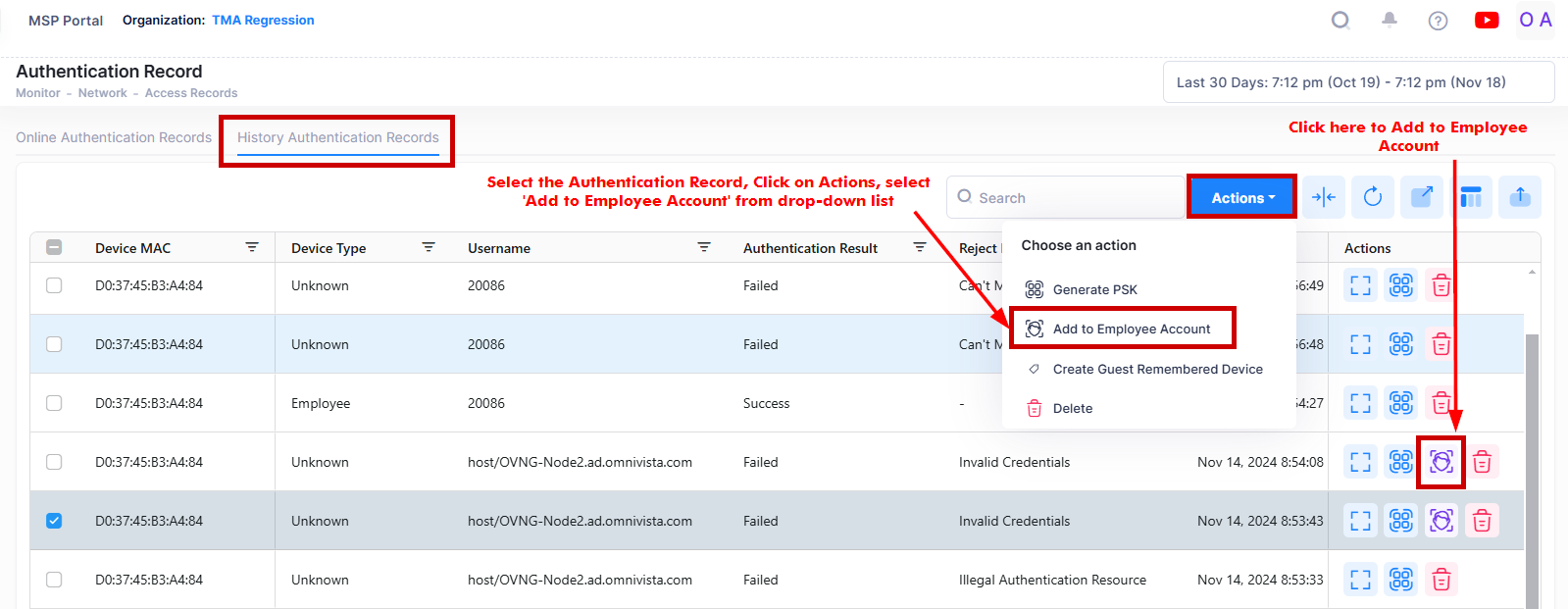
The Add to Employee Account will open below screen.
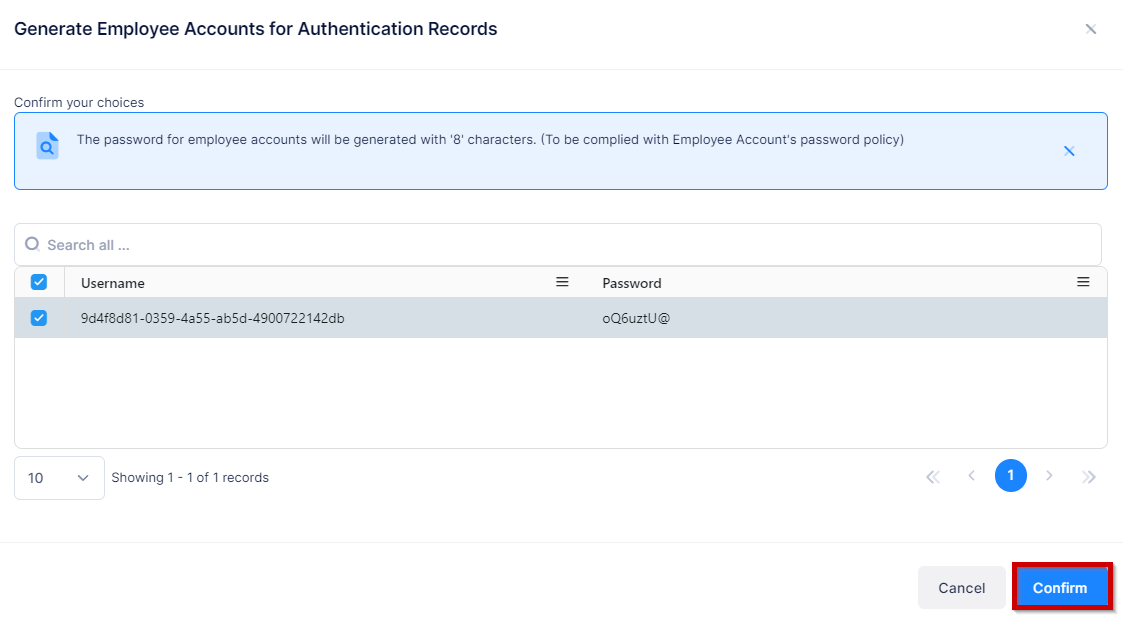
Click on Confirm to generate the Employee Account for an User in the Authentication Records.
The password for employee accounts will be generated with '8' characters. (To be complied with Employee Account's password policy).
You can also search and add multiple Authentication Records from the list to generate the Employee account.
The Add to Employee Account action button appears under all of the following conditions together:
Authentication Result = Failed
Authentication Resource = Local Database
Authentication Type = 802.1X or Portal
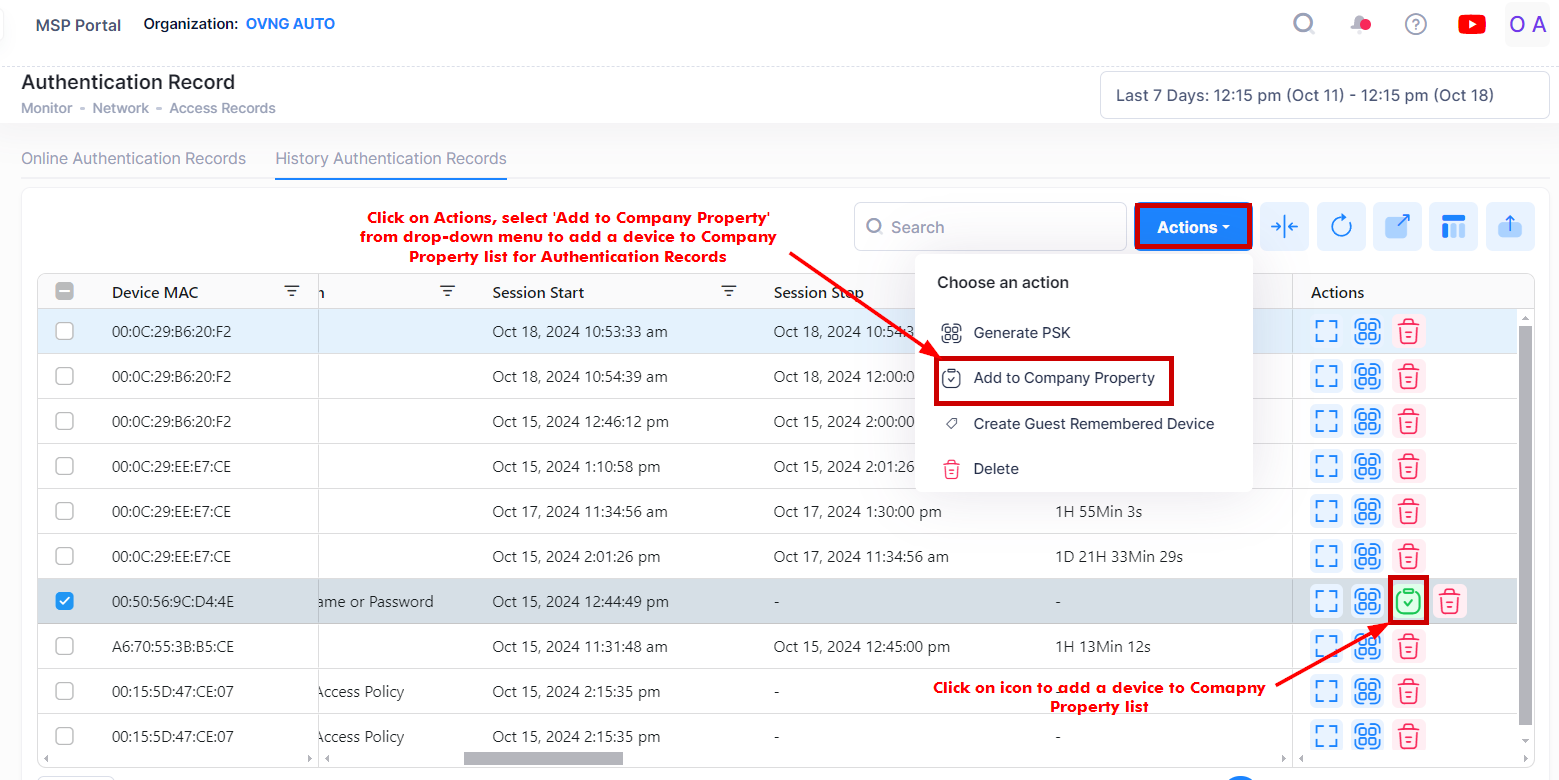
Add to a Company Property
To add network devices to Company Property list for Authentication records, select the records in the History Authentication Records list and click on Actions, then select Add to Company Property from the drop-down menu. You can also click on the Add to Company Property icon under the “Actions” column next to an individual record.
The Add to Company Property List will open below screen.
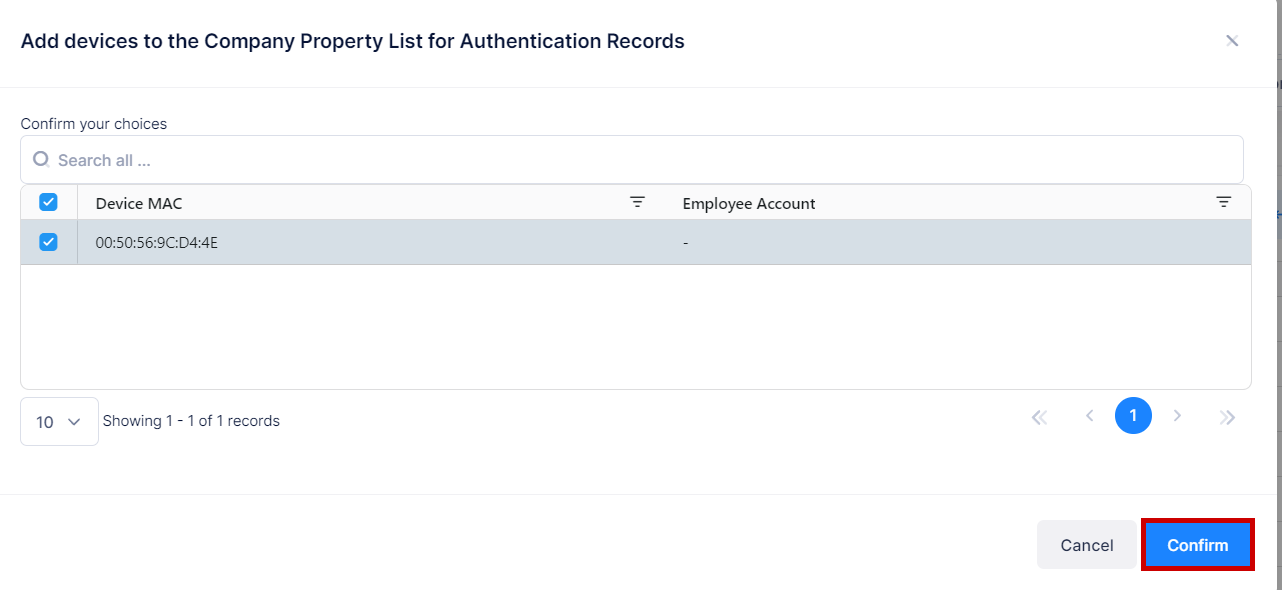
Click on Confirm to add the device to the Company Property List for the Authentication Records.
Note: The Add to Company Property action button appears under all of the following conditions together:
Authentication Result = Failed
Authentication Resource = Local Database
Authentication Type = MAC
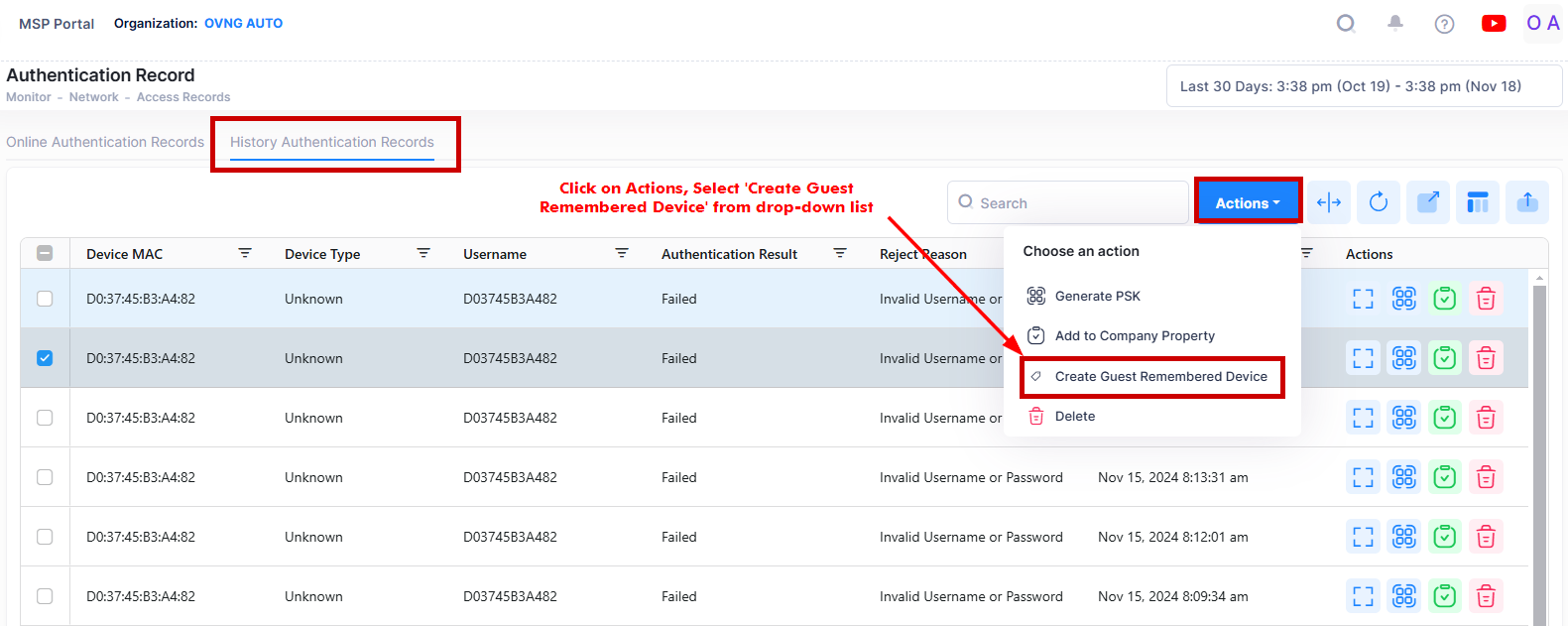
Create Guest Remembered Device
To create a Guest Remembered Device for the Authentication Records, select the records in the History Authentication Records list and click on Actions, then select Create Guest Remembered Device from the drop-down menu.
It directs you to Create Guest Remembered Device Screen as shown below:
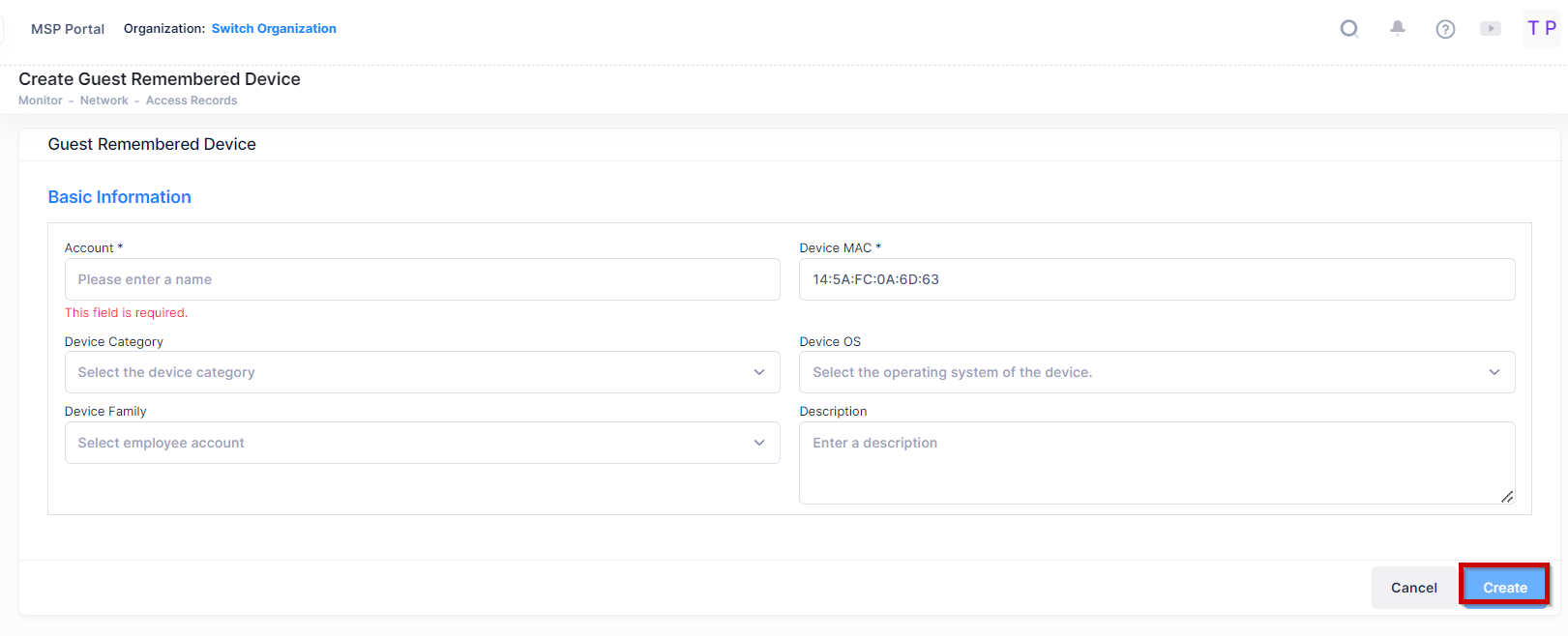
Enter the required information in the fields and click on Create button to create the Guest Remembered Device for the Authentication Records.
Log a User Out of the Network (Delete)
To delete an Authentication Record for one or more devices, select the records in the History Authentication Records List and click on Actions, then select Delete from the drop-down menu. You can also click on the Delete icon under the “Actions” column next to an individual record.
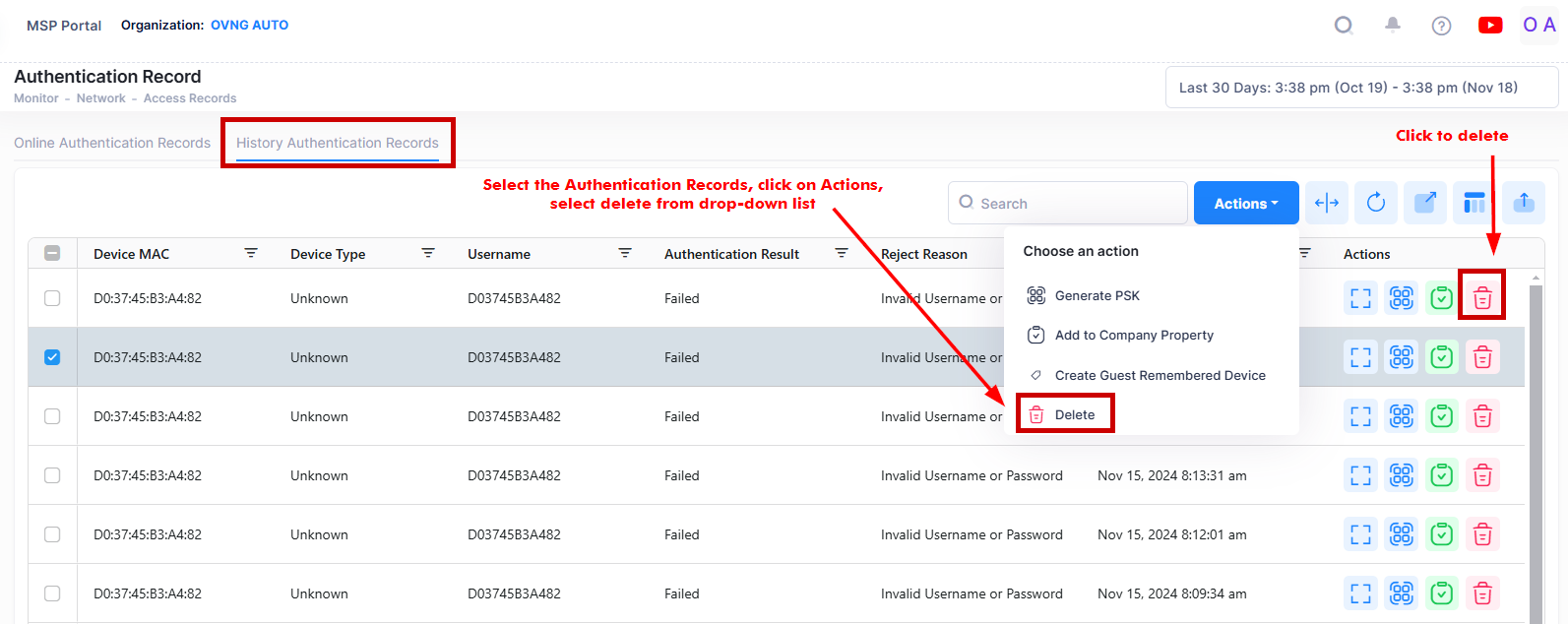
Click Delete on the following confirmation prompt. Note that when you delete an Authentication Record, you are logging the user associated with that record out of the network.
Authentication Records List
The Authentication Record List displays basic information for all Authentication Records. Click on the Additional Information icon under the “Actions' column next to a list entry to display detailed Authentication Record Information. The following screen appears:
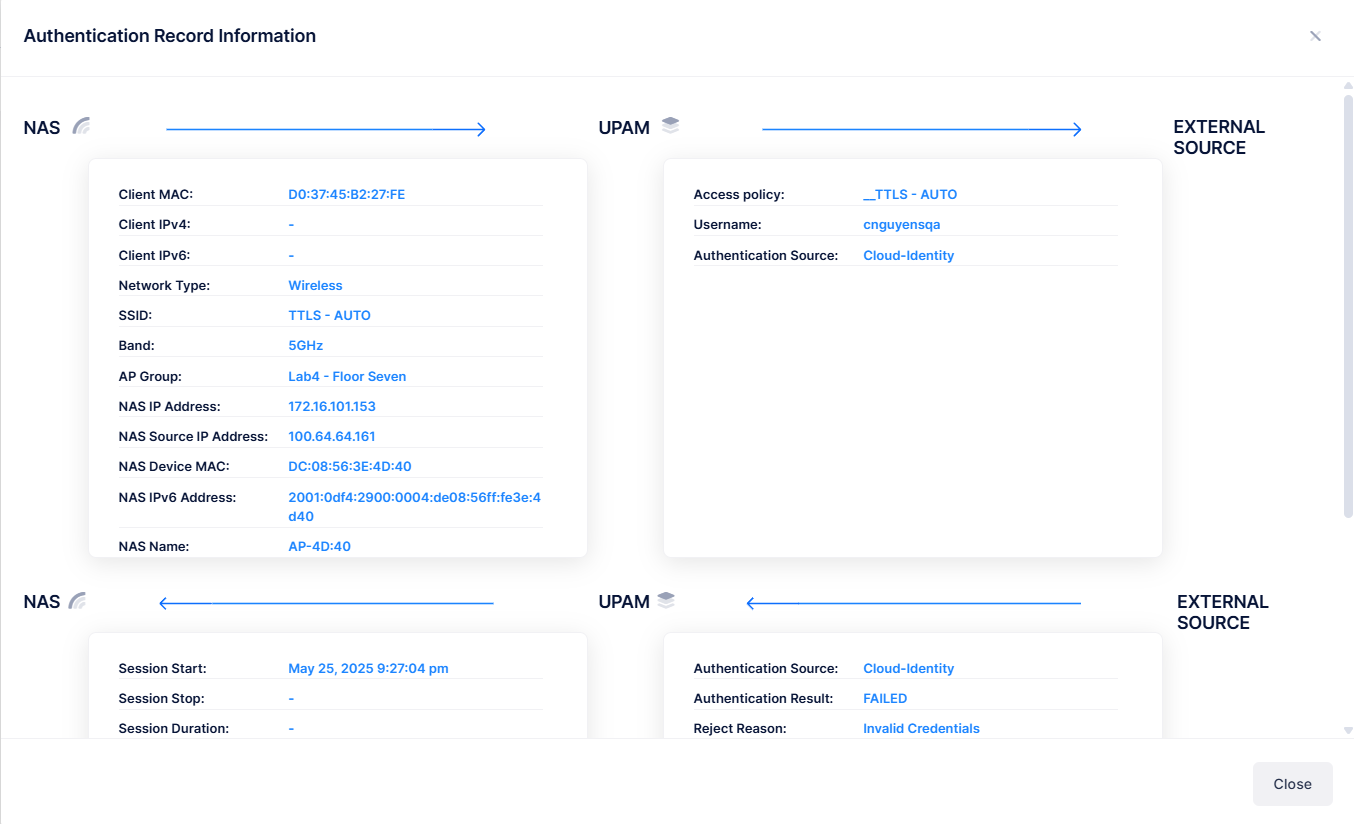
The Authentication Record field values provide the following information:
Client MAC - The MAC address of the user device requesting authentication.
Client IPv4 - The IPv4 address of the client of the user device requesting authentication. Note that IP addresses are displayed only if they are known at the time the RADIUS Accounting packets are sent/received. For MAC Authentication, the Accounting Start packets typically do not contain client IP addresses.
Client IPv6 - The IPv6 address of the client of the user device requesting authentication. Note that IP addresses are displayed only if they are known at the time the RADIUS Accounting packets are sent/received. For MAC Authentication, the Accounting Start packets typically do not contain client IP addresses.
SSID - The access device SSID.
Band - The frequency band used for NAS Client.
AP Group - AP Group through which you accesses the network.
Device Type - The type of the device.
Username - User name of the device requesting authentication.
Authentication Result - Result for the user authentication request (Success, Failed).
Reject Reason - Reason for rejecting the authentication request from user device:
Overdue license
Invalid username or password
Cannot match access policy according to the authentication request.
Session Start - The time when the user passed authentication and a connection session was created.
Session Stop - The time when the connection session was terminated..
Session Time - It specifies the maximum number of seconds of service provided prior to session termination..
Account Terminate Cause - The reason for which the connection session was terminated..
Account Session ID - Unique accounting ID that makes it easy to match start and stop records in a log file. The start and stop records for a given session must have the same account session ID.
Account Multi Session ID - This is a unique accounting ID to make it easy to link together multiple related sessions in a log file.
Authentication Type - The type of authentication used for the device (e.g., MAC, 802.1X)
Authentication method - The method used for the device Authentication.(e.g., PAP, EAP-MD5, EAP-PEAP, EAP-TLS).
Auth Resource - User profile database used in authentication, including none, local database, LDAP/AD and external RADIUS server, can refer to the authentication strategy definition.
Network Type - The type of network used for device authentication. (Wireless or Wired).
NAS IP Address - The identifying IP address of the NAS.
NAS Source IP Address - The source IP address of the NAS.
NAS IPv6 Address - The IPv6 address of the NAS.
NAS Name - The Alcatel device name.
Packet Arrival - The date and time at which the packet is received.
Packet Type - The specific type of RADIUS message being transmitted between the client (NAS) and the RADIUS server.
EAP Method - The specific method of Extensible Authentication Protocol (EAP) technique used within RADIUS to perform user authentication.
Alcatel Tenant ID - It is the unique identifier of a specific tenant.
Alcatel Device SSID - Wireless service broadcast by the NAS and connected by user device (only valid for wireless access).
NAS ID - NAS Identifier, identify the NAS originating the Access-Request.
NAS Port Type - The type of physical port type of the NAS authenticating the user:
Wireless-IEEE 802.11
Ethernet.
Called Station ID - Allows the NAS to send the phone number the user called, using Dialed Number Identification (DNIS) or similar technology inside the Access-Request packet:
For Switch - Switch MAC Address.
For AP - radio_MAC_address:SSID_NAME.
NAS Port - The physical port number of the NAS authenticating the user.
For Switch - if index.
For AP - Wireless radio index.
Service Type - It is a standard attribute (Service-Type) used in RADIUS authentication requests and responses to specify the type of service being requested or provided to the user.
Alcatel Port desc - The NAS Port description.
For Switch - Port description.
For AP - WLAN service.
NAS Port ID - The NAS authenticating the user.
For Switch - chassis/slot/port
For AP - WLAN service.
Framed MTU - The Maximum Transmission Unit to be configured for the user when it is not negotiated by some other means (e.g., PPP). It is a fixed value = 1400.
Alcatel Device MAC - MAC address of the NAS to which the user device is attached.
Alcatel Device Name - System name of the NAS to which the user device is attached.
Alcatel Device Location - Location of the NAS.
NAS Device MAC - The MAC address of the NAS Device.
Access Device SSID - Wireless service broadcast by the NAS and connected by user device (only valid for wireless access).
Total UPAM Transactions - The total time taken to complete RADIUS authentication.
Access Policy - Name of the Access Policy for the user.
Web Access Policy - Guest Strategy or BYOD Strategy.
Final Access Role Profile - Access Role Profile assigned by NAS and in effect on the user device, but not the Access Role Profile returned by UPAM.
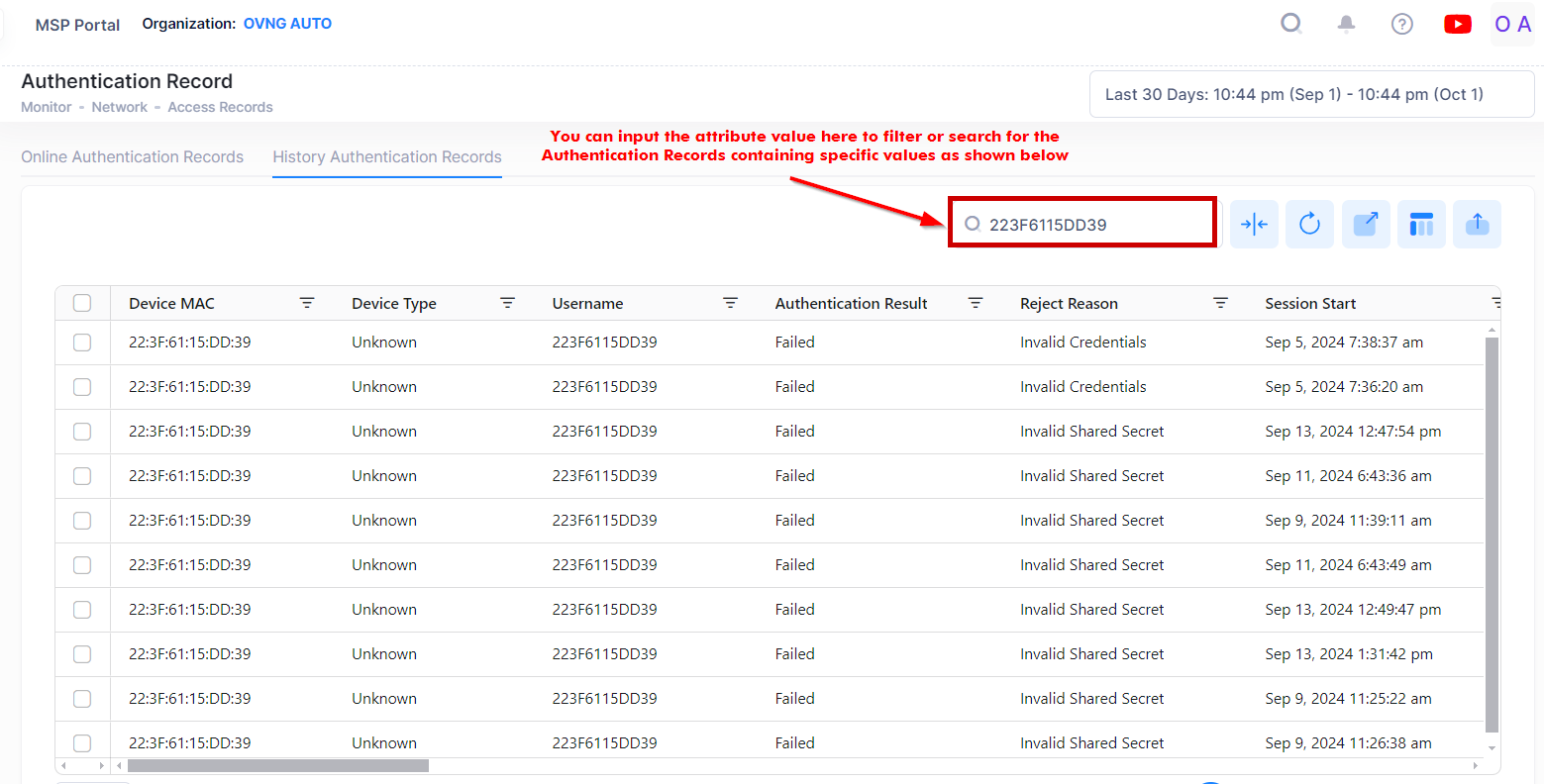
Search History Authentication Records by an Attribute Value
You can search for history Authentication records by using the Search box option. The search results are refined based on the attribute value selected from the available list (Device MAC/Nas Device MAC/Access Device SSID or Username). Only those records that contain the matching searched values are displayed in the results.