WIPS Clients Analytics
The “WIPS Clients” section of the Monitor WIPS Analytics dashboard includes widgets that show the the Rogue Clients, Blocklisted Clients and DeAuth Clients Table associated with the managed devices during the specified time window range.
Data displayed in each widget can be exported into a CSV, PDF or Excel sheet format. You can also switch the widgets to full-screen mode for a better display.
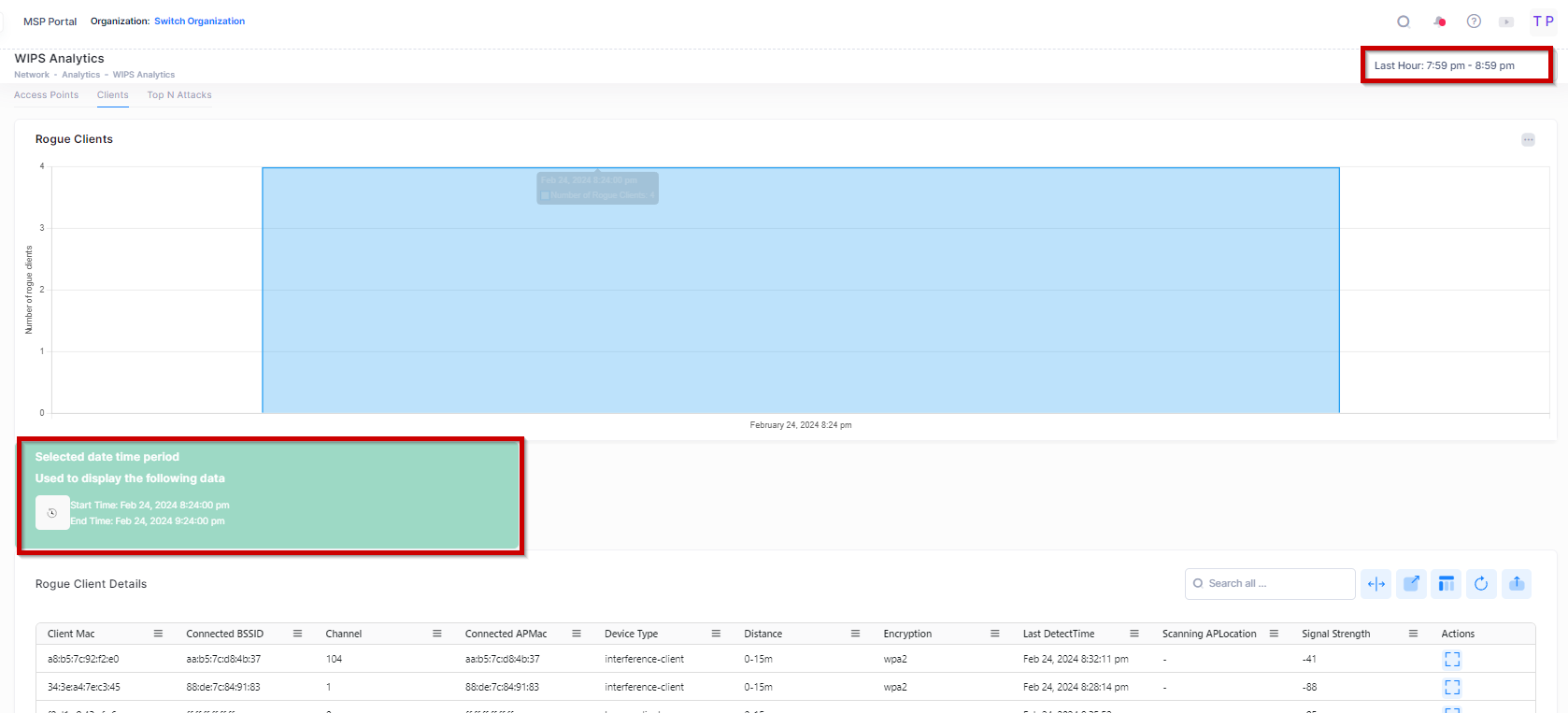
The “Select time” option is used to select the date and period by clicking on one of the bars from the chart to display the other related WIPS Client Analytics metrics on the screen.
By default, the bar chart selects and displays the latest available Client details for the last hour range. The time interval between two points in the chart is 5 minutes when the last hour is selected from the filter, but the ‘Rogue Client Details’ table displays data for the complete last hour. The Chart bar data is not clickable for the last hour’s time duration.
However, for other ranges (like 6,12 ,24 hour, etc.), the time interval between two points is one hour, and by default, the latest data point is selected. You can click anywhere on the bar chart to see the detail Analytics and all related Chart details for a specific time duration as shown below:
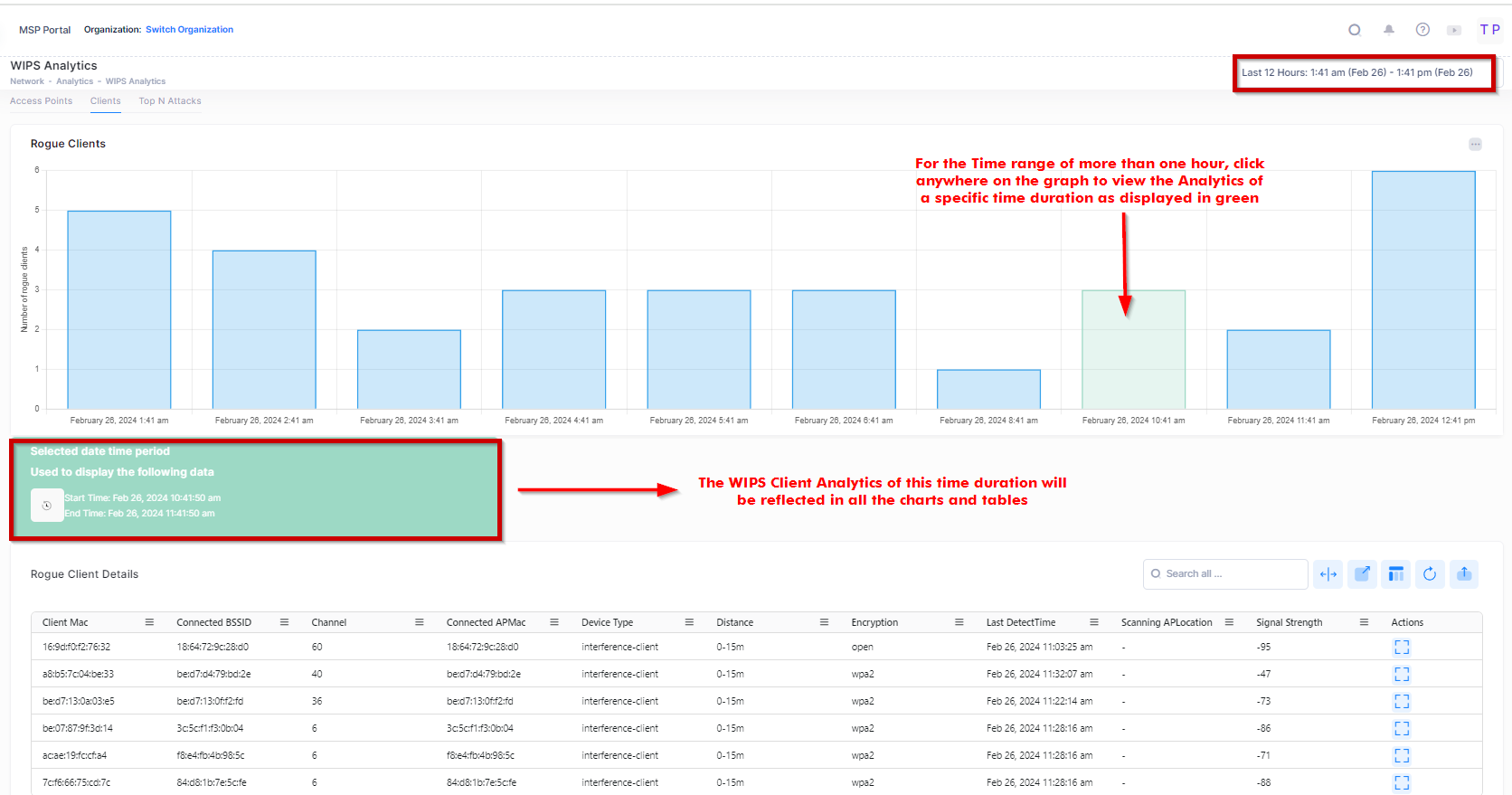
For each Rogue client details table, the following attribute values are provided:
Client MAC - MAC address of the rogue client.
Connected BSSID - BSSID of the interfering AP to which the client is associated.
Connected SSID - ESSID to which the rogue associated.
Channel - Working channel of the rogue client.
Connected APMac - MAC address of the valid AP that detected the interfering AP.
Device type - The type of the device.
Distance - Distance between the rogue client and the detecting AP.
Encryption - Encryption method of the SSID to which the rogue client is associated.
Signal Strength - RSSI of the rogue client.
Last Detected Time - The latest time that the rogue client was seen by the detecting AP.
Scanning AP Location - Location of the valid AP that detected the interfering AP.
Reason - Indicates the reason for classifying the foreign AP as a rogue AP:
Signal Strength is Too Strong, Reducing Network Performance
Channel is Switching Too Often
Broadcasting Conflicted SSID, Misleading User Connection
Matching the Keyword of Suspected SSID
Matching the Suspected MAC OUI
Time Stamp from scanning AP - The first time when the rogue client was seen by the detecting AP.